The Latest Spying Revelations: SIM Cards and Hard Drives
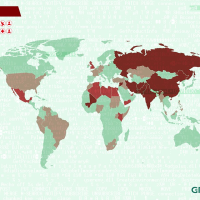 Equation Family Victims Map (graphic: Kaspersky Lab)
Equation Family Victims Map (graphic: Kaspersky Lab)
The computer or phone on which you’re reading this article might be doing double duty right now—sending information back to U.S. and British intelligence agencies via the hardware in the device.
For those on your phones, know that there’s a good chance that your SIM card has been compromised. That small piece of plastic known as a Subscriber Identity Module is produced by one of a few manufacturers and sold to your phone company. The largest manufacturer of those cards, Gemalto, was mentioned in documents turned over by whistleblower Edward Snowden to The Intercept as having been penetrated by the National Security Agency (NSA) and its British counterpart, GCHQ.
GCHQ planted malware on Gemalto computers, which enabled the agency to steal the encryption keys the company put on SIMs sold to AT&T, Verizon, Sprint, T-Mobile and other wireless companies around the world. A GCHQ presentation obtained by The Intercept noted “that the spy agency was ‘very happy with the data so far and [was] working through the vast quantity of product.’ ”
As well it should be. Having the key makes it a snap to read all the information, whether voice or data, coming from a phone. “Once you have the keys, decrypting traffic is trivial,” Christopher Soghoian, principal technologist for the American Civil Liberties Union, told The Intercept. “The news of this key theft will send a shock wave through the security community.”
Ah, but my laptop or desktop doesn’t have a SIM, you say. Right, but it does have a hard drive and a report from Russian anti-virus company Kaspersky Labs shows that a suite of programs it calls “The Equation Family” has infected hard drives for more than a decade. The malicious code lives in the firmware, or basic software that controls a hard drive. That code remains even if a hard drive is reformatted and a new operating system, such as Windows or Mac OS, is reinstalled.
The Equation Family malware, which was reportedly developed by the NSA, served as a test version of the Stuxnet virus that infected Iranian computers and delayed its nuclear program. It can give intelligence agencies control of an infected computer for years and can be installed with innocuous-seeming promotional CDs or USB sticks. “As we uncover more of these cyber espionage operations we realize how little we understand about the true capabilities of these threat actors,” Costin Raiu, head of Kaspersky’s Global Research and Analysis Team, told Wired.
Kaspersky says the malware has likely infected tens of thousands of computers, primarily in Iran, but also in Russia, Afghanistan, Pakistan, Belgium, Germany, Sudan, Lebanon, the Palestinian Territories, the United States and the United Kingdom.
-Steve Straehley
To Learn More:
The Great SIM Heist (by Jeremy Scahill and Josh Begley, The Intercept)
Suite of Sophisticated Nation-State Attack Tools Found With Connection to Stuxnet (by Kim Zetter, Wired)
How the NSA’s Firmware Hacking Works and Why It’s So Unsettling (by Kim Zetter, Wired)
Russian Researchers Uncover Sophisticated NSA Malware (by Eva Galperin and Cooper Quintin, Electronic Frontier Foundation)
Equation: The Death Star of Malware Galaxy (Kapersky Lab)
Stuxnet Attack on Iran…the Worm that Keeps on Giving (by Noel Brinkerhoff, AllGov)
- Top Stories
- Unusual News
- Where is the Money Going?
- Controversies
- U.S. and the World
- Appointments and Resignations
- Latest News
- Trump Orders ICE and Border Patrol to Kill More Protestors
- Trump Renames National Football League National Trump League
- Trump to Stop Deportations If…
- Trump Denounces World Series
- What If China Invaded the United States?






Comments